1. Introduction & Overview
✅ What Are OTA Updates?
Over-the-Air (OTA) Updates refer to the remote delivery of software, firmware, or configuration updates to embedded systems or devices via wireless communication channels. Commonly used in IoT, automotive, mobile, and embedded environments, OTA ensures devices remain current without needing physical access.
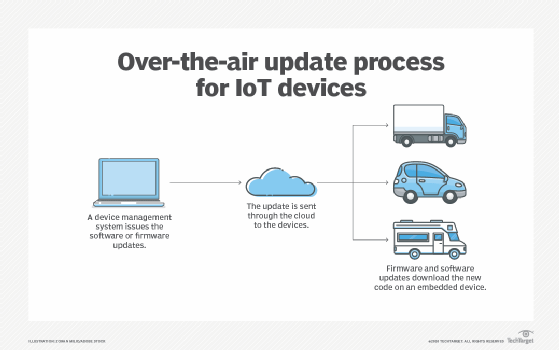
📜 History & Background
- Early Use: Started in mobile networks for updating baseband firmware and device software.
- Expansion: Gained traction in IoT, automotive ECUs, and connected appliances.
- Modern Applications: OTA is critical in continuous deployment pipelines for edge devices and cloud-integrated environments.
🔐 Why It’s Relevant in DevSecOps
- Remote Patch Management: Vital for pushing security patches to distributed fleets.
- Agile Security Fixes: Supports rapid deployment of vulnerability fixes.
- CI/CD Compatibility: Integrates well with pipelines to automate device updates.
- Compliance: Meets cybersecurity requirements for devices (e.g., ISO 21434, IEC 62443).
2. Core Concepts & Terminology
🔑 Key Terms
| Term | Definition |
|---|---|
| OTA Update | Wireless transfer of firmware/software to remote devices. |
| Firmware | Low-level software that controls device hardware. |
| Update Agent | Software running on device, responsible for applying updates. |
| Update Server | Central component that hosts and dispatches updates. |
| Delta Updates | Only differences (patches) between versions are transmitted. |
| Rollback | Reverting to the previous known-good version. |
| Secure Boot | Verifies update integrity at startup using cryptographic checks. |
🔄 OTA in DevSecOps Lifecycle
| DevSecOps Phase | OTA Relevance |
|---|---|
| Plan | Define update scope, security policies. |
| Develop | Code for updatable firmware/software with update hooks. |
| Build | Package updates in secure, signed containers. |
| Test | Simulate updates in staging environments. |
| Release | Push updates via CI/CD to production OTA servers. |
| Deploy | OTA agents pull/apply updates. Monitor rollout progress. |
| Operate | Track device state, failures, versioning. |
| Monitor | Integrate with logging/metrics systems (e.g., Prometheus, ELK). |
3. Architecture & How It Works
🧱 Components
- OTA Client/Agent: Resides on devices; checks for updates, downloads, verifies, and applies them.
- OTA Server: Manages update versions, authorization, device groups.
- Update Repository: Stores binary files, metadata, signatures.
- Security Module: Signs updates and verifies authenticity (e.g., using GPG, X.509).
- CI/CD Pipeline: Automates build, sign, and upload processes.
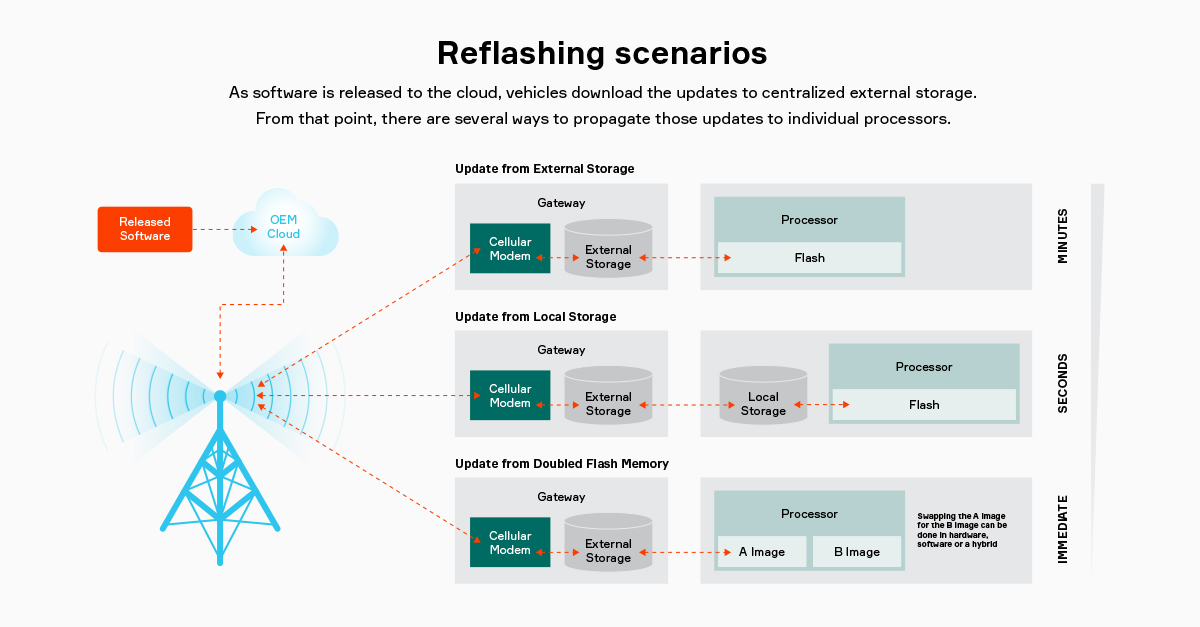
🔁 Workflow
- Build Phase:
- CI compiles firmware/software.
- Updates are signed using private keys.
- Upload Phase:
- Secure transfer to OTA server or object storage.
- Metadata is generated and published.
- Deployment Phase:
- OTA agent checks for updates (polling or pushed).
- Downloads delta or full update.
- Verifies hash/signature.
- Applies the update and reboots if necessary.
- Reports status back to OTA server.
🧭 Architecture Diagram (Described)
+---------------+ +------------------+ +------------------+
| CI/CD System | -----> | OTA Update Server| -----> | Update Repository|
+---------------+ +------------------+ +------------------+
| ^ |
v | v
+---------------+ +------------------+ +------------------+
| Security Signer| -----> | Device Registry | <----- | Monitoring Stack |
+---------------+ +------------------+ +------------------+
^
|
+-----------------+
| OTA Client/Agent|
| (on Devices) |
+-----------------+
🔗 Integration with CI/CD & Cloud Tools
| Tool | Integration Use |
|---|---|
| Jenkins/GitLab CI | Build, package, and sign updates. |
| AWS IoT Core | OTA Jobs and device shadow updates. |
| Azure IoT Hub | Device twin sync and update delivery. |
| Kubernetes | Manage OTA server instances via Helm. |
| HashiCorp Vault | Secure signing key management. |
4. Installation & Getting Started
⚙️ Prerequisites
- A Linux/Unix system (Ubuntu preferred)
- Docker & Docker Compose
- Git
- GPG or OpenSSL (for signing)
- Python 3.x or Node.js (depending on tooling)
- Devices or emulators supporting OTA agents (e.g., Raspberry Pi, ESP32)
🚀 Step-by-Step Beginner Setup (Using Hawkbit)
1. Clone Hawkbit OTA server repo:
git clone https://github.com/eclipse/hawkbit.git
cd hawkbit
2. Start Hawkbit with Docker:
docker-compose up -d
3. Access UI:
http://localhost:8080
Username: admin
Password: admin
4. Create Target Group (Device Group)
Use the admin UI to register your devices.
5. Simulate Device Client (using REST API or MQTT)
curl -X GET http://localhost:8080/rest/v1/targets
6. Upload & Deploy Update Artifact
- Upload signed
.binor.tar.gzfile. - Assign to a rollout campaign.
5. Real-World Use Cases
📌 Use Case 1: IoT Security Patch Management
- Deploy urgent CVE patches to smart sensors via OTA.
- Monitored via Prometheus/Grafana dashboards.
📌 Use Case 2: Automotive ECU Update
- Push updates to in-vehicle ECUs securely.
- Rollback mechanism ensures fail-safe deployment.
📌 Use Case 3: Consumer Electronics
- Smart TVs receive firmware updates with new features.
- OTA client embedded into firmware.
📌 Use Case 4: Industrial Control Systems
- PLCs and SCADA systems updated during maintenance windows.
- OTA ensures minimal downtime and audit compliance.
6. Benefits & Limitations
✅ Key Advantages
- Zero-touch deployment: No physical intervention needed.
- Fast rollouts: Critical fixes can be patched instantly.
- Scalable: Handle millions of devices concurrently.
- Secure by design: Supports cryptographic validation.
⚠️ Common Limitations
| Limitation | Description |
|---|---|
| Connectivity issues | Updates fail in poor network conditions. |
| Bricking risk | Improper updates can render devices inoperable. |
| Device memory constraints | Large updates may not fit in flash memory. |
| Rollback complexity | Requires additional bootloader and partition setup. |
7. Best Practices & Recommendations
🔐 Security Tips
- Use TLS/HTTPS for update transport.
- Sign updates using GPG or x.509 certificates.
- Implement secure boot and chain of trust.
⚙️ Performance & Maintenance
- Use delta updates to reduce bandwidth.
- Schedule updates during off-peak hours.
- Implement watchdogs for update failures.
📋 Compliance & Automation
- Ensure audit logs for update campaigns.
- Automate rollout via GitOps-style pipelines.
- Align with standards like NIST SP 800-53, ISO/SAE 21434.
8. Comparison with Alternatives
| Approach | OTA Updates | Manual Updates | A/B Partitioning OTA | Container OTA |
|---|---|---|---|---|
| Automation | ✅ High | ❌ Low | ✅ Medium | ✅ High |
| Security | ✅ High (if signed) | ❌ Unverified | ✅ High | ✅ High |
| Rollback | ⚠️ Medium (needs setup) | ❌ Manual only | ✅ Easy rollback | ⚠️ Depends |
| Scalability | ✅ Massive fleets | ❌ Limited | ✅ Medium | ✅ Cloud-native |
When to Choose OTA:
- Devices are remote or physically inaccessible.
- High frequency of updates or patches.
- Need cryptographic verification and audit trails.
- Part of a DevSecOps CI/CD flow.
9. Conclusion
OTA updates are a cornerstone of modern DevSecOps practices in connected systems, enabling secure, scalable, and automated delivery of software across devices. As edge computing and IoT continue to grow, robust OTA strategies become essential for resilience, compliance, and performance.