1. Introduction & Overview
What is Code Signing?
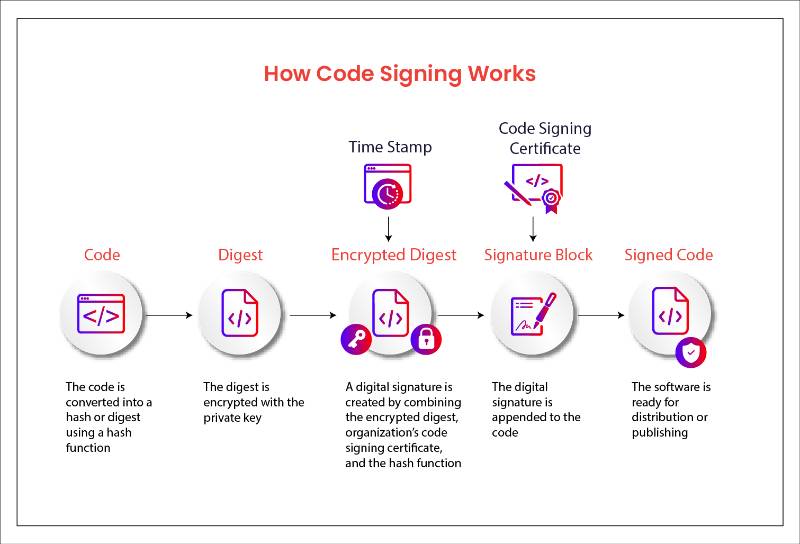
Code Signing is the process of digitally signing executables, scripts, firmware, or software packages to verify the authenticity and integrity of the code. It ensures that the software:
- Comes from a trusted source (authorship verification).
- Has not been tampered with since being signed (integrity check).
- Is safe for execution on devices, including robots.
In RobotOps—the operational discipline of managing robotic software lifecycle—Code Signing becomes critical. Robots often rely on updates over-the-air (OTA) or from centralized CI/CD pipelines, and without verification, they could be vulnerable to malicious code injections.
History or Background
- Early 1990s: First adoption of digital signatures for software distribution.
- Microsoft Authenticode (1996): Formalized code signing for Windows applications.
- Mobile ecosystems (2007 onwards): Apple and Android mandated signed applications.
- Robotics era: With autonomous robots operating in critical industries (healthcare, defense, manufacturing), Code Signing became essential to ensure trust in robotic software updates.
Why is it Relevant in RobotOps?
In RobotOps, reliability and safety are paramount. A single corrupted firmware update could:
- Cause operational downtime.
- Lead to unsafe robotic behavior.
- Violate compliance and safety standards.
Thus, Code Signing ensures:
- Robust trust chain between developers and deployed robots.
- Safe OTA updates without manual supervision.
- Compliance with standards like ISO 10218 (industrial robots), IEC 62443 (cybersecurity in automation).
2. Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Private Key | Secret key used by developers or CI/CD pipelines to sign the code. |
| Public Key | Distributed to robots/devices to verify authenticity of signed code. |
| Digital Signature | Encrypted hash of the code proving it has not been altered. |
| Certificate Authority (CA) | Trusted entity issuing certificates for signing identities. |
| Hashing | Process of creating a unique fingerprint of code (e.g., SHA-256). |
How it Fits into the RobotOps Lifecycle
- Development → Developers write code for robotic software.
- Build → CI/CD pipeline compiles firmware or software packages.
- Sign → Build artifacts are signed with a private key.
- Deploy → Robots receive updates over-the-air (OTA).
- Verify → Robot firmware checks the signature before execution.
- Operate → Safe execution with trust assurance.
3. Architecture & How It Works
Components
- Developer/CI Pipeline: Produces and signs code.
- Signing Server (HSM recommended): Stores private keys securely.
- Robots/Devices: Validate signatures with pre-installed public keys.
- Certificate Authority: Issues certificates for identity validation.
Internal Workflow
- Developer commits code.
- CI/CD builds firmware/software.
- Signing server applies digital signature using private key.
- Signed artifact is distributed (OTA, package manager).
- Robot validates signature with public key before execution.
Architecture Diagram (Described)
Imagine a flow diagram:
- Left side: Developers → CI/CD pipeline → Signing server.
- Middle: Signed package stored in repository.
- Right side: Robots pull updates → Verify with public key → Execute only if verified.
Integration Points with CI/CD or Cloud Tools
- GitHub Actions →
signing-actionto sign builds. - Jenkins → Integrate
signtoolorosslsigncode. - AWS IoT Device Management → Verifies signed firmware updates.
- Azure IoT Hub → Supports code signing for OTA robotic firmware.
4. Installation & Getting Started
Prerequisites
- Linux/Windows/macOS build environment.
- OpenSSL or platform-specific signing tool.
- Access to a private key and certificate.
Hands-On Setup (Beginner Friendly)
Step 1: Generate Keys
# Generate a private key
openssl genrsa -out robotops_private.pem 2048
# Extract public key
openssl rsa -in robotops_private.pem -pubout -out robotops_public.pem
Step 2: Sign Code (example: firmware.bin)
openssl dgst -sha256 -sign robotops_private.pem -out firmware.sig firmware.bin
Step 3: Verify Signature on Robot
openssl dgst -sha256 -verify robotops_public.pem -signature firmware.sig firmware.bin
Output:
Verified OK
5. Real-World Use Cases
Scenario 1: Autonomous Delivery Robots
- OTA firmware signed before fleet-wide deployment.
- Prevents hackers from hijacking delivery bots with rogue updates.
Scenario 2: Medical Robots in Hospitals
- Surgical robots verify updates via signatures to ensure patient safety.
- Meets compliance with healthcare cybersecurity regulations.
Scenario 3: Industrial Robotics in Manufacturing
- Factory robots receive frequent software patches.
- Code Signing ensures only authorized vendor updates are installed.
Scenario 4: Military & Defense Drones
- Strict enforcement of signed firmware prevents adversaries from injecting malware.
6. Benefits & Limitations
Key Advantages
- Trust & Integrity: Only authenticated code runs.
- Compliance: Aligns with ISO, IEC, HIPAA, and defense standards.
- Security: Mitigates supply chain attacks.
- Automation: Fits into CI/CD with minimal overhead.
Limitations
- Key Management Complexity (HSM recommended).
- Performance Overhead (verification step before execution).
- Certificate Expiry (requires renewal).
- Initial Setup Cost for CA and infrastructure.
7. Best Practices & Recommendations
- Store private keys in Hardware Security Modules (HSMs).
- Rotate keys regularly.
- Automate signing in CI/CD pipelines.
- Enforce mandatory verification on all robots before execution.
- Monitor for certificate revocation.
- Use timestamping services to ensure validity even after certificate expiration.
8. Comparison with Alternatives
| Approach | Pros | Cons | Use Case |
|---|---|---|---|
| Code Signing | Strong trust, compliance ready, CI/CD friendly | Key management complexity | RobotOps OTA updates |
| Checksum Only | Lightweight, simple | No identity/authenticity guarantee | Non-critical robotics scripts |
| Access Control | Prevents unauthorized update sources | Doesn’t check code integrity | Internal robot test labs |
| Container Signing (e.g., Cosign) | Cloud-native, works with Kubernetes | Requires containerized workflows | Cloud-connected robot fleets |
9. Conclusion
Code Signing is the backbone of secure RobotOps.
By ensuring that every robotic update is signed and verified, organizations can:
- Build trust in autonomous systems.
- Prevent cyberattacks on robots.
- Stay compliant with industry regulations.
Future Trends
- Integration with Zero Trust Robotics Security.
- Blockchain-based code signing to prevent certificate forgery.
- AI-powered anomaly detection in signature verification.
Next Steps
- Start small with OpenSSL-based signing.
- Gradually integrate cloud-native signing services (AWS/Azure).
- Use HSMs for key storage in production RobotOps environments.