1. Introduction & Overview
What is Robot Lifecycle Management?
Robot Lifecycle Management (RLM) refers to the end-to-end administration, governance, security, and orchestration of software robots—primarily in Robotic Process Automation (RPA) environments. These “robots” are software agents that emulate human actions in digital systems, and their lifecycle includes development, deployment, operation, monitoring, and retirement.
History or Background
- Early RPA Tools (2000s): Initial RPA tools like Blue Prism and UiPath emerged to automate repetitive tasks.
- Shift Toward Enterprise RPA (2015–2020): As RPA adoption grew, managing robot sprawl became complex, giving rise to the need for structured lifecycle management.
- Integration with DevOps/DevSecOps: Organizations began integrating RLM with CI/CD and security pipelines for scalable, secure automation.
Why is it Relevant in DevSecOps?
- Security Enforcement: Automates policy application, access control, and secret management.
- Compliance: Maintains audit trails and regulatory alignment.
- CI/CD Integration: Enables robots to be versioned, tested, and deployed like traditional code.
- Minimizes Risk: Ensures robots are not misconfigured or outdated, reducing attack surfaces.
2. Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Robot | A software agent that performs rule-based tasks in systems. |
| RPA | Robotic Process Automation, a technology to automate business processes. |
| Robot Orchestration | Coordinating execution, scaling, and monitoring of bots. |
| Bot Deployment Pipeline | A CI/CD-style process for testing and deploying bots. |
| Robot Repository | A version-controlled store for bot code, configurations, and artifacts. |
| Robot Retirement | Secure decommissioning of obsolete or vulnerable bots. |
How It Fits into the DevSecOps Lifecycle
| DevSecOps Phase | Role of RLM |
|---|---|
| Plan | Define automation use cases and governance policies. |
| Develop | Use source control and secure coding standards for bot creation. |
| Build | Automate testing and packaging of bots. |
| Release | Deploy bots through approved pipelines. |
| Operate | Monitor and orchestrate bots at runtime. |
| Secure | Implement identity management, RBAC, and vulnerability scans. |
3. Architecture & How It Works
Core Components
- Bot Development Environment: IDE or low-code tools like UiPath Studio or Automation Anywhere.
- Version Control System (VCS): Git repositories storing robot scripts and configuration.
- Bot Repository / Artifact Store: Stores compiled bots (e.g., Azure Artifacts, Artifactory).
- CI/CD Pipelines: Automate testing, approval, and deployment of bots.
- Bot Orchestrator: Schedules and distributes bots (e.g., UiPath Orchestrator).
- Security & Audit Layer: Enforces access policies, audit logging, and compliance.
- Monitoring Tools: Track bot health, errors, and KPIs.
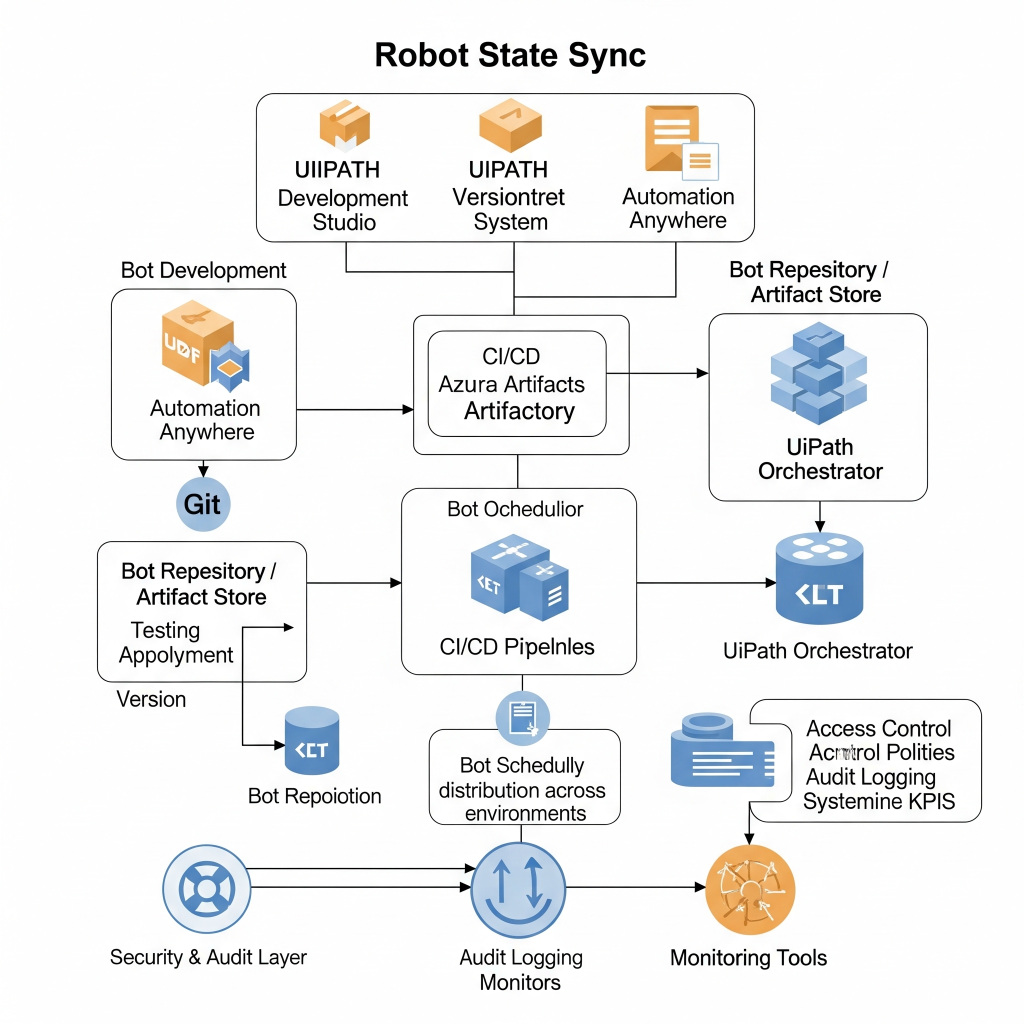
Architecture Diagram Description
[Bot Dev IDE] -> [Git Repository] -> [CI/CD Pipeline]
↓ ↓
[Static/Dynamic Scanning] [Artifact Store]
↓ ↓
[Secure Deployment] -> [Bot Orchestrator]
↓
[Target Systems]
↓
[Audit Logs]
Integration Points with CI/CD or Cloud Tools
- CI Tools: Jenkins, GitHub Actions, GitLab CI
- Artifact Stores: Nexus, JFrog Artifactory
- Security: HashiCorp Vault (for secrets), SonarQube (code analysis)
- Cloud: AWS Step Functions, Azure Logic Apps, Google Cloud Workflows
4. Installation & Getting Started
Basic Setup or Prerequisites
- Git installed and access to version control.
- Access to an RPA tool (e.g., UiPath Community, Automation Anywhere).
- Jenkins or GitLab CI setup.
- Access to an orchestration platform.
Hands-on: Beginner-Friendly Setup Guide
Step 1: Clone an RPA Bot Repository
git clone https://github.com/example-org/rpa-bot-repo.git
cd rpa-bot-repo
Step 2: Create CI/CD Pipeline (Example: GitHub Actions)
# .github/workflows/bot-ci.yml
name: Bot CI Pipeline
on: [push]
jobs:
build:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v2
- name: Install RPA CLI
run: pip install rpaframework
- name: Run Lint & Unit Tests
run: rpa lint && rpa test
Step 3: Deploy Bot to Orchestrator (e.g., UiPath Cloud)
uipathcli login --client-id xxx --client-secret yyy
uipathcli deploy --path ./output/bot.zip --env PROD
Step 4: Monitor Execution
- Check logs from orchestrator dashboard.
- Review audit trail and performance metrics.
5. Real-World Use Cases
1. Continuous Compliance Enforcement
Deploy bots that scan infrastructure for misconfigurations (e.g., open S3 buckets), then report or auto-remediate.
2. Automated Threat Intelligence
Bots fetch CVEs and push updates into security dashboards or trigger security patching pipelines.
3. Credential Rotation
Robots periodically rotate secrets in HashiCorp Vault or AWS Secrets Manager and propagate changes.
4. Incident Response Automation
When SIEM alerts fire, bots quarantine resources, notify stakeholders, and file a Jira ticket.
6. Benefits & Limitations
Key Advantages
- Scalability: Thousands of bots can be managed uniformly.
- Security: Enforces least privilege, secrets management, and audit logging.
- Operational Efficiency: Speeds up repetitive, rule-based security and ops tasks.
- Compliance: Centralized logging and versioning aid in audits.
Common Challenges
| Challenge | Description |
|---|---|
| Robot Sprawl | Uncontrolled creation of bots leads to management overhead. |
| Secret Management | Bots require credentials; mishandling leads to leaks. |
| Toolchain Complexity | Integrating CI/CD, RPA, and security requires orchestration skills. |
| Governance | Requires strict RBAC, naming conventions, and lifecycle policies. |
7. Best Practices & Recommendations
Security Tips
- Always use secret vaults (e.g., HashiCorp, AWS Secrets Manager).
- Apply RBAC and MFA to orchestrator access.
- Perform static analysis on bot code before deployment.
Performance Optimization
- Schedule bots during off-peak hours to avoid resource contention.
- Use telemetry to identify and optimize long-running bots.
Compliance Alignment
- Maintain version history of all bots.
- Log bot actions and use immutable storage (e.g., Amazon S3 with WORM).
Automation Ideas
- Auto-tagging bots with metadata.
- Auto-retirement of inactive bots.
- Auto-redeployment on infrastructure change.
8. Comparison with Alternatives
| Feature | Robot Lifecycle Management | Traditional RPA | IAC Tools (e.g., Terraform) |
|---|---|---|---|
| Security Automation | ✅ | ❌ | ⚠️ |
| CI/CD Integration | ✅ | ❌ | ✅ |
| Bot Governance | ✅ | ❌ | ❌ |
| Human Workflow Automation | ✅ | ✅ | ❌ |
| Infrastructure Automation | ❌ | ❌ | ✅ |
When to Choose RLM
- You have more than 10 bots in production.
- Regulatory compliance requires audit trails.
- You want to enforce security and lifecycle policies.
- You need bots to integrate with cloud or CI/CD.
9. Conclusion
Robot Lifecycle Management brings DevSecOps discipline into RPA environments. It ensures that bots are versioned, secure, and compliant throughout their lifecycle. By combining CI/CD, security scanning, secrets management, and orchestration, RLM empowers teams to scale automation while maintaining control and trust.
Next Steps
- Adopt RLM as part of your DevSecOps platform.
- Standardize your robot development and deployment process.
- Monitor and audit robot performance regularly.