Introduction & Overview
Key rotation is a critical security practice in RobotOps, the discipline of managing, deploying, and operating robotic systems. It involves periodically replacing cryptographic keys, API tokens, or access credentials to minimize the risk of unauthorized access or data breaches. In RobotOps, where robots interact with cloud platforms, CI/CD pipelines, and diverse hardware, secure key management ensures safe communication and operation.
This tutorial provides a comprehensive guide to implementing key rotation in RobotOps, covering its definition, history, integration, and practical applications. It is designed for technical readers, including roboticists, DevOps engineers, and security professionals, who aim to secure robotic systems effectively.
What is Key Rotation?
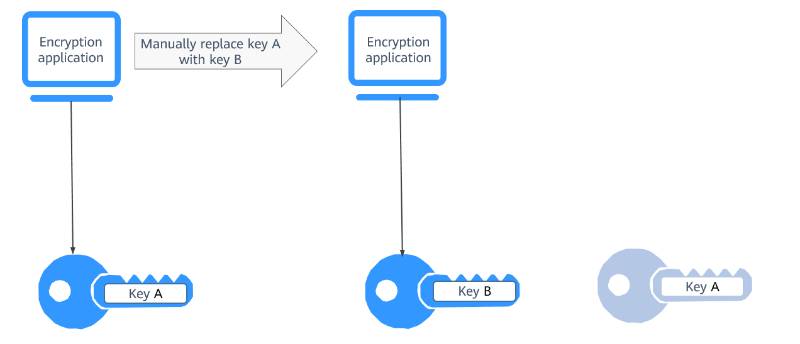
Key rotation is the process of periodically updating cryptographic keys or access credentials used in systems to authenticate, encrypt, or decrypt data. In RobotOps, this applies to keys used for robot-to-cloud communication, API access, or secure device authentication.
- Definition: Replacing old keys with new ones to limit exposure to compromised credentials.
- Purpose: Enhances security by reducing the window of opportunity for attackers to exploit stolen or leaked keys.
- Scope in RobotOps: Key rotation is applied to robotic systems interacting with cloud platforms (e.g., AWS, Azure), CI/CD pipelines (e.g., Jenkins), or frameworks like Robot Operating System (ROS) and Robot Framework.
History or Background
Key rotation emerged as a security best practice in the early days of cryptography, particularly in military and financial systems, to protect sensitive communications. With the rise of cloud computing and IoT in the 2000s, key rotation became critical for securing distributed systems, including robotic deployments.
- Early Cryptography (Pre-2000s): Manual key rotation in military systems, such as Enigma, to prevent decryption by adversaries.
- Cloud and IoT Era (2000s–2010s): Automated key rotation gained prominence with cloud providers like AWS introducing services like AWS Key Management Service (KMS) in 2014.
- RobotOps Context (2010s–Present): The adoption of ROS and Robot Framework in robotic systems necessitated secure key management for cloud-integrated robots, especially in industries like manufacturing and healthcare.
Why is it Relevant in RobotOps?
RobotOps involves managing fleets of robots that communicate with cloud services, process sensor data, and integrate with CI/CD pipelines for updates. Key rotation is vital for:
- Security: Protects against unauthorized access to robotic systems.
- Compliance: Meets standards like GDPR, HIPAA, or ISO 27001 for data protection.
- Scalability: Ensures secure management of credentials across large robot fleets.
- Reliability: Prevents service disruptions due to compromised keys.
Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Key Rotation | Periodic replacement of cryptographic keys or credentials to enhance security. |
| Cryptographic Key | A string of bits used to encrypt/decrypt data or authenticate systems. |
| API Token | A secure token used for authenticating API calls between robots and services. |
| RobotOps | The practice of managing, deploying, and operating robotic systems. |
| ROS (Robot Operating System) | An open-source framework for robot software development. |
| Robot Framework | A keyword-driven test automation framework used in RobotOps. |
| CI/CD Pipeline | Continuous Integration/Continuous Deployment for automating robot updates. |
How It Fits into the RobotOps Lifecycle
Key rotation integrates into the RobotOps lifecycle at several stages:
- Development: Secure API keys for testing robotic applications.
- Deployment: Rotating keys during robot provisioning to cloud platforms.
- Operation: Periodic key updates to maintain secure communication.
- Monitoring: Auditing key usage to detect anomalies or breaches.
- Maintenance: Replacing expired or compromised keys to ensure uptime.
Architecture & How It Works
Components and Internal Workflow
Key rotation in RobotOps involves several components:
- Key Management Service (KMS): Centralized service (e.g., AWS KMS, HashiCorp Vault) for generating, storing, and rotating keys.
- Robot Nodes: Individual robots or ROS nodes that use keys for authentication or encryption.
- Authentication Service: Verifies robot identities using keys or tokens.
- CI/CD Pipeline: Automates key rotation during software updates.
- Monitoring Tools: Track key usage and detect unauthorized access.
Workflow:
- A robot requests a key from the KMS during initialization.
- The KMS generates and distributes a new key, invalidating the old one.
- The robot updates its configuration with the new key.
- CI/CD pipelines trigger key rotation during deployments.
- Monitoring tools log key usage for auditing.
Architecture Diagram
Below is a textual description of the key rotation architecture in RobotOps:
+------------------+ +------------------+ +------------------+
| Developer/CI | -----> | Vault/KMS API | -----> | Robot Fleet |
| (Jenkins/GitHub) | | (Key Generation) | | (API, SSH, TLS) |
+------------------+ +------------------+ +------------------+
| | |
v v v
+---------------+ +-----------------+ +----------------+
| Monitoring & | <--------> | Rotation Events | <------> | Audit & Logs |
| Alert System | | Controller | | (Compliance) |
+---------------+ +-----------------+ +----------------+
- Robot Fleet: Multiple robots running ROS nodes.
- ROS Nodes: Communicate with cloud services using API keys.
- Authentication Service: Validates keys for secure access.
- KMS: Manages key generation, rotation, and revocation.
- CI/CD Pipeline: Integrates key rotation into deployment workflows.
- Monitoring System: Logs key usage and alerts on anomalies.
Integration Points with CI/CD or Cloud Tools
- CI/CD Tools (e.g., Jenkins, GitLab CI):
- Automate key rotation during robot software updates.
- Example: Jenkins pipeline triggers AWS KMS to rotate keys.
- Cloud Platforms (e.g., AWS, Azure):
- Use managed services like AWS KMS or Azure Key Vault for key storage.
- Integrate with ROS for secure robot-to-cloud communication.
- Robot Framework:
Installation & Getting Started
Basic Setup or Prerequisites
- Python 3.8+: Required for Robot Framework and scripting.
- ROS 2: For robotic system integration.
- AWS CLI or Azure CLI: For cloud-based key management.
- Robot Framework: For testing key rotation workflows.
- HashiCorp Vault (Optional): For advanced key management.
- Docker: For containerized environments.
Install prerequisites:
# Install Python
sudo apt-get install python3 python3-pip
# Install ROS 2 (Humble, for Ubuntu 22.04)
sudo apt-get install software-properties-common
sudo add-apt-repository ppa:ros/ppa
sudo apt-get install ros-humble-desktop
# Install Robot Framework
pip install robotframework
# Install AWS CLI
pip install awscli
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
- Set Up AWS KMS:
- Log in to AWS Management Console.
- Navigate to Key Management Service (KMS) and create a new symmetric key.
- Enable automatic key rotation (recommended: yearly).
2. Configure ROS 2 Node:
- Create a ROS 2 package for key management:
ros2 pkg create --build-type ament_python key_rotation- Add a Python script (
key_rotator.py) to fetch and update keys:
import boto3
import rclpy
from rclpy.node import Node
class KeyRotator(Node):
def __init__(self):
super().__init__('key_rotator')
self.kms_client = boto3.client('kms')
self.timer = self.create_timer(3600, self.rotate_key)
def rotate_key(self):
response = self.kms_client.create_key()
new_key_id = response['KeyMetadata']['KeyId']
self.get_logger().info(f'Rotated to new key: {new_key_id}')
def main():
rclpy.init()
node = KeyRotator()
rclpy.spin(node)
rclpy.shutdown()
if __name__ == '__main__':
main()3. Integrate with Robot Framework:
- Create a Robot Framework test case (
key_rotation_test.robot):
*** Settings ***
Library OperatingSystem
Library Process
*** Test Cases ***
Verify Key Rotation
${result}= Run Process python3 key_rotator.py
Should Contain ${result.stdout} Rotated to new key4. Run the Test:
- Execute the test case:
robot key_rotation_test.robot5. Set Up CI/CD Pipeline:
- Create a Jenkins pipeline to automate key rotation:
pipeline {
agent any
stages {
stage('Rotate Key') {
steps {
sh 'aws kms create-key'
sh 'robot key_rotation_test.robot'
}
}
}
}Real-World Use Cases
- Manufacturing Robot Fleet:
- Scenario: A factory uses ROS-based robots for assembly. Key rotation secures API calls to a cloud-based control system.
- Implementation: AWS KMS rotates keys every 90 days, integrated with Jenkins for automated updates.
- Industry: Manufacturing.
- Healthcare Robotics:
- Scenario: Surgical robots transmit patient data to a cloud platform. Key rotation ensures HIPAA compliance.
- Implementation: Azure Key Vault rotates keys monthly, with Robot Framework tests verifying compliance.
- Industry: Healthcare.
- Logistics Automation:
- Scenario: Autonomous delivery robots communicate with a fleet management system. Key rotation prevents unauthorized access.
- Implementation: HashiCorp Vault rotates API tokens daily, integrated with GitLab CI.
- Industry: Logistics.
- Construction Robotics:
Benefits & Limitations
Key Advantages
- Enhanced Security: Reduces risk of key compromise.
- Compliance: Aligns with GDPR, HIPAA, and ISO 27001.
- Automation: Integrates with CI/CD for seamless updates.
- Scalability: Supports large robot fleets with centralized key management.
Common Challenges or Limitations
- Complexity: Managing key rotation across heterogeneous robots is challenging.
- Downtime Risk: Improper rotation can disrupt robot operations.
- Cost: Cloud-based KMS services incur costs.
- Learning Curve: Requires familiarity with ROS, Robot Framework, and cloud tools.
Best Practices & Recommendations
- Security Tips:
- Use strong, unique keys with at least 256-bit encryption.
- Store keys in a secure KMS like AWS KMS or HashiCorp Vault.
- Audit key usage regularly with monitoring tools.
- Performance:
- Schedule rotations during low-traffic periods to minimize disruptions.
- Use asynchronous key updates to avoid latency in robot operations.
- Maintenance:
- Test key rotation workflows using Robot Framework before deployment.
- Maintain a backup of old keys for recovery.
- Compliance Alignment:
- Align rotation frequency with compliance requirements (e.g., monthly for HIPAA).
- Document rotation policies for audits.
- Automation Ideas:
- Integrate key rotation with CI/CD pipelines for automatic updates.
- Use Robot Framework to validate key rotation in test environments.
Comparison with Alternatives
| Feature/Tool | Key Rotation (KMS-Based) | Manual Key Management | Secret Management (e.g., Vault) |
|---|---|---|---|
| Automation | High (CI/CD integration) | Low (Manual updates) | High (Automated policies) |
| Scalability | High (Cloud-based) | Low (Error-prone) | High (Centralized) |
| Security | High (Encrypted storage) | Medium (Human errors) | High (Advanced policies) |
| Cost | Medium (Cloud fees) | Low (No tools) | High (Enterprise setup) |
| RobotOps Integration | Excellent (ROS, CI/CD) | Poor (Manual) | Good (Custom integrations) |
When to Choose Key Rotation:
- Use KMS-based key rotation for large-scale, cloud-integrated RobotOps deployments.
- Opt for manual key management for small, isolated systems with low security needs.
- Choose secret management tools like Vault for complex, multi-system environments.
Conclusion
Key rotation is a cornerstone of secure RobotOps, ensuring robotic systems remain protected against unauthorized access and comply with industry standards. By integrating with ROS, Robot Framework, and CI/CD pipelines, key rotation enhances the reliability and scalability of robotic deployments.
Future Trends:
- AI-Driven Rotation: Machine learning to predict optimal rotation schedules.
- Zero Trust Architecture: Continuous key validation for enhanced security.
- Edge Computing: Localized key management for low-latency robot operations.
Next Steps:
- Explore AWS KMS or Azure Key Vault documentation for setup guides.
- Join the Robot Framework community (http://robotframework.org) or ROS community (http://ros.org) for support.
- Experiment with the provided code snippets in a test environment.
Resources: