Introduction & Overview
What is Role-Based Access Control (RBAC)?
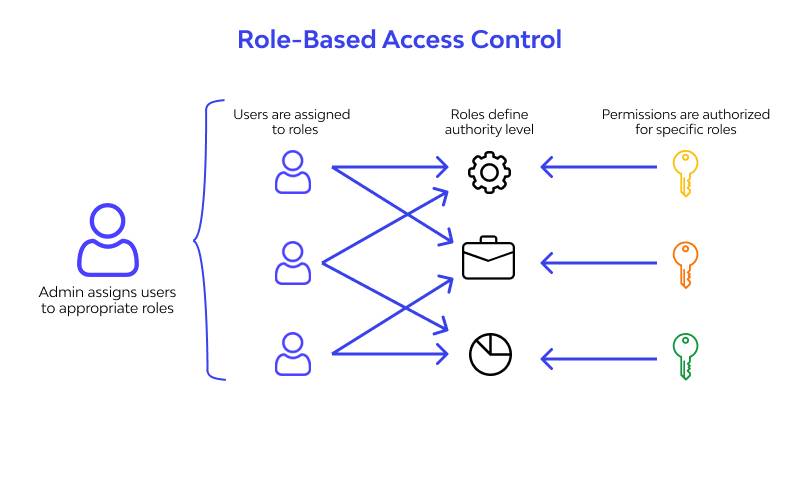
Role-Based Access Control (RBAC) is a security model that restricts system access to authorized users based on their roles within an organization. In RBAC, permissions are assigned to roles rather than individual users, and users are assigned to one or more roles, inheriting the associated permissions. This approach simplifies access management, enhances security, and ensures compliance with the principle of least privilege (PoLP), where users only access resources necessary for their tasks.
History or Background
RBAC’s origins trace back to the 1970s when early computer systems used ad-hoc access control methods. These were inefficient and lacked scalability. In 1992, researchers David Ferraiolo and Rick Kuhn at the National Institute of Standards and Technology (NIST) formalized RBAC in a seminal paper, proposing a structured model for civilian and commercial use. Their work introduced a framework where permissions were grouped into roles, streamlining access management. Throughout the 1990s and early 2000s, NIST refined RBAC, incorporating concepts like separation of duties (SoD) and role hierarchies. In 2004, NIST officially adopted RBAC as an industry standard, cementing its place in modern security practices.
- 1970s: Ad-hoc access control methods in early computing systems.
- 1992: Ferraiolo and Kuhn’s paper lays the foundation for RBAC.
- 1996–2000: NIST refines RBAC, introducing models like RBAC0, RBAC1, RBAC2, and RBAC3.
- 2004: RBAC becomes a NIST standard, widely adopted across industries.
- Present: RBAC is integral to cloud platforms, DevOps, and RobotOps, evolving with dynamic and hierarchical implementations.
Why is it Relevant in RobotOps?
RobotOps, the operational framework for managing robotic systems, involves complex workflows, including robot deployment, monitoring, and maintenance, often in distributed environments. RBAC is critical in RobotOps for:
- Security: Protects sensitive robotic systems and data from unauthorized access.
- Scalability: Simplifies permission management for large teams and fleets of robots.
- Compliance: Aligns with regulations like GDPR, HIPAA, or ISO 27001, ensuring auditable access controls.
- Automation: Integrates with CI/CD pipelines and cloud tools to streamline robot lifecycle management.
- Collaboration: Enables role-specific access for diverse teams (e.g., developers, operators, and auditors) in RobotOps workflows.
Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| User | An individual or entity (e.g., human, robot, or service) accessing the system. |
| Role | A named collection of permissions reflecting a job function or responsibility. |
| Permission | An allowed action (e.g., read, write, deploy) on a specific resource. |
| Session | A temporary context where a user activates one or more roles to access resources. |
| Role Hierarchy | A structure where higher-level roles inherit permissions from lower-level roles. |
| Separation of Duties (SoD) | A constraint preventing a single user from holding conflicting roles (e.g., deployer and auditor). |
| Principle of Least Privilege (PoLP) | Users are granted only the minimum permissions needed for their tasks. |
How It Fits into the RobotOps Lifecycle
The RobotOps lifecycle includes stages like design, development, deployment, monitoring, and maintenance of robotic systems. RBAC integrates at each stage:
- Design & Development: Developers access code repositories and simulation tools based on roles (e.g., “Robot Developer”).
- Deployment: Deployment engineers have permissions to push robot configurations to production environments.
- Monitoring: Operators access dashboards and logs to monitor robot performance without altering configurations.
- Maintenance: Maintenance teams access diagnostic tools but are restricted from modifying core robot logic.
RBAC ensures that each stage is secure, auditable, and aligned with organizational policies, reducing risks in automated robotic operations.
Architecture & How It Works
Components
RBAC in RobotOps comprises the following components:
- Users: Humans (e.g., engineers, operators) or automated agents (e.g., CI/CD bots).
- Roles: Defined job functions like “Robot Operator,” “Fleet Manager,” or “Security Auditor.”
- Permissions: Specific actions (e.g., deploy_robot, view_logs, update_config) tied to resources (e.g., robot fleets, databases).
- Role Assignments: Mappings of users to roles.
- Policy Enforcement Point (PEP): Validates user requests against RBAC policies.
- Policy Decision Point (PDP): Evaluates permissions and makes access decisions.
- Policy Repository: Stores role and permission definitions.
Internal Workflow
- A user initiates a request (e.g., deploy a robot configuration).
- The PEP intercepts the request and forwards it to the PDP.
- The PDP checks the user’s role(s) and associated permissions in the policy repository.
- The PDP returns an allow/deny decision based on the role’s permissions.
- The PEP enforces the decision, granting or denying access.
Architecture Diagram
Below is a textual description of the RBAC architecture in RobotOps (since image generation is not possible):
+------------------+ +------------------+
| User/Service |-----> | Authentication |
| (Dev, Ops, Bot) | | (SSO/IAM/OAuth) |
+------------------+ +------------------+
|
v
+---------------------+
| RBAC Policy Engine|
| (Roles & Permissions)|
+---------------------+
|
-------------------------------------------
| | |
+---------------+ +---------------+ +---------------+
| Robot Fleet | | CI/CD Pipelines| | Monitoring DB |
+---------------+ +---------------+ +---------------+
- User: Initiates actions via a CLI, UI, or API.
- PEP: A gateway (e.g., RobotOps CLI or API) that enforces access control.
- PDP: The decision-making engine (e.g., integrated with Kubernetes RBAC or AWS IAM).
- Policy Repository: A database or configuration file storing role-permission mappings.
- Authentication Service: Verifies user identity (e.g., via OAuth, LDAP).
- RobotOps Resources: Robots, fleets, or data stores accessed based on permissions.
Integration Points with CI/CD or Cloud Tools
RBAC integrates seamlessly with RobotOps tools:
- CI/CD Pipelines: Tools like Jenkins or GitLab use RBAC to control who can trigger robot builds or deployments.
- Cloud Platforms: AWS IAM, Azure RBAC, or Kubernetes RBAC manage access to robot-related cloud resources.
- Monitoring Tools: Platforms like Prometheus or Grafana use RBAC to restrict dashboard access.
- Orchestrators: Kubernetes RBAC controls access to robot pods and services.
Installation & Getting Started
Basic Setup or Prerequisites
To implement RBAC in a RobotOps environment, ensure:
- A RobotOps platform (e.g., ROS 2, Kubernetes-based robot orchestrator).
- An authentication system (e.g., OAuth, LDAP, or cloud IAM).
- A policy management tool (e.g., Open Policy Agent, AWS IAM, or Kubernetes RBAC).
- Administrative access to configure roles and permissions.
- A database or configuration store for policy storage.
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
This guide demonstrates setting up RBAC in a Kubernetes-based RobotOps environment.
- Install Kubernetes Cluster:
Ensure a Kubernetes cluster is running (e.g., Minikube for testing or EKS for production).
minikube start2. Enable RBAC in Kubernetes:
Verify RBAC is enabled (default in Kubernetes 1.6+).
kubectl api-versions | grep rbac3. Define Roles:
Create a YAML file (robot-operator-role.yaml) for a “Robot Operator” role.
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
namespace: robotops
name: robot-operator
rules:
- apiGroups: [""]
resources: ["pods"]
verbs: ["get", "list", "watch"]
- apiGroups: ["robotops.io"]
resources: ["robots"]
verbs: ["view", "monitor"]4. Apply the Role:
kubectl apply -f robot-operator-role.yaml5. Create RoleBinding:
Bind the role to a user or group (robot-operator-binding.yaml).
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
name: robot-operator-binding
namespace: robotops
subjects:
- kind: User
name: operator1
apiGroup: rbac.authorization.k8s.io
roleRef:
kind: Role
name: robot-operator
apiGroup: rbac.authorization.k8s.io6. Apply the RoleBinding:
kubectl apply -f robot-operator-binding.yaml7. Test Access:
Authenticate as operator1 and verify access to robot resources.
kubectl auth can-i get pods --namespace=robotops --as=operator18. Monitor and Audit:
Use Kubernetes audit logs to track access decisions.
kubectl logs -n kube-system
Real-World Use Cases
- Warehouse Automation:
- Scenario: A logistics company uses a fleet of autonomous robots for inventory management.
- RBAC Application: Roles like “Warehouse Operator” (view inventory status), “Robot Technician” (update robot firmware), and “Fleet Manager” (deploy new robots) ensure secure access to robot control systems.
- Industry Example: Amazon Robotics uses RBAC to restrict access to its Kiva robots, ensuring only authorized personnel can modify robot paths or access inventory data.
- Healthcare Robotics:
- Scenario: Surgical robots in a hospital require strict access controls to comply with HIPAA.
- RBAC Application: Roles like “Surgeon” (operate robot), “Technician” (calibrate robot), and “Auditor” (view logs) enforce compliance and security.
- Industry Example: Intuitive Surgical’s da Vinci system uses RBAC to limit access to patient data and robot controls.
- Industrial Manufacturing:
- Scenario: A factory deploys robots for assembly line tasks.
- RBAC Application: Roles like “Line Operator” (monitor robots), “Maintenance Engineer” (repair robots), and “Supervisor” (configure workflows) streamline operations.
- Industry Example: Tesla’s Gigafactory uses RBAC to control access to robotic arms and production data.
- Research and Development:
- Scenario: A robotics lab develops experimental robots.
- RBAC Application: Roles like “Researcher” (access simulation tools), “Developer” (write robot code), and “Admin” (manage lab resources) ensure secure collaboration.
- Industry Example: Boston Dynamics uses RBAC to protect proprietary robot algorithms.
Benefits & Limitations
Key Advantages
| Benefit | Description |
|---|---|
| Simplified Management | Assigning permissions to roles reduces complexity compared to per-user permissions. |
| Enhanced Security | Enforces PoLP and SoD, minimizing unauthorized access risks. |
| Scalability | Easily accommodates new users or role changes in growing RobotOps environments. |
| Compliance | Provides auditable access logs for regulatory requirements (e.g., GDPR, HIPAA). |
| Operational Efficiency | Streamlines access provisioning and reduces administrative overhead. |
Common Challenges or Limitations
| Limitation | Description |
|---|---|
| Role Explosion | Overdefining roles for specific tasks can lead to management complexity. |
| Lack of Context | RBAC lacks dynamic attributes (e.g., time, location) for fine-grained control. |
| Initial Setup Effort | Defining roles and permissions requires thorough organizational analysis. |
| Privilege Creep | Temporary roles or exceptions may persist, increasing security risks. |
Best Practices & Recommendations
- Follow PoLP: Assign only the minimum permissions needed for each role.
- Implement Role Hierarchies: Use hierarchical roles to inherit permissions (e.g., “Senior Operator” inherits from “Operator”).
- Regular Audits: Periodically review roles and permissions to prevent privilege creep.
- Automate RBAC: Use tools like Ansible or Terraform to automate role assignments.
- Integrate with IAM: Leverage cloud IAM (e.g., AWS IAM, Azure AD) for centralized access control.
- Train Stakeholders: Educate teams on RBAC policies to ensure compliance.
- Compliance Alignment: Map roles to regulatory requirements (e.g., ISO 27001, PCI DSS).
- Monitor Access: Use logging tools (e.g., Kubernetes audit logs, CloudTrail) to track access.
Comparison with Alternatives
| Model | Description | Pros | Cons | When to Use |
|---|---|---|---|---|
| RBAC | Permissions assigned to roles, users inherit roles. | Simple, scalable, auditable. | Lacks context, role explosion risk. | Large teams, static roles. |
| ABAC | Permissions based on attributes (e.g., user, resource, environment). | Fine-grained, context-aware. | Complex to manage, higher overhead. | Dynamic, attribute-rich environments. |
| ACL | Permissions assigned directly to users or resources. | Highly granular, simple for small setups. | Unscalable for large systems. | Small-scale, user-specific access. |
| ReBAC | Permissions based on relationships between entities (e.g., manager-employee). | Handles complex hierarchies. | Complex to implement, maintain. | Relation-rich environments. |
When to Choose RBAC
- Choose RBAC: When managing large teams with well-defined job functions in RobotOps, where simplicity and scalability are priorities.
- Choose Alternatives: Use ABAC for dynamic, context-aware access (e.g., time-based robot control) or ReBAC for hierarchical relationships (e.g., robot fleet ownership).
Conclusion
RBAC is a cornerstone of secure and efficient access management in RobotOps, offering simplicity, scalability, and compliance. By assigning permissions to roles, RBAC ensures that robotic systems are protected from unauthorized access while streamlining operations across the RobotOps lifecycle. Despite challenges like role explosion, careful planning and adherence to best practices mitigate these issues. As RobotOps evolves with AI and distributed systems, RBAC will adapt, potentially integrating with ABAC or ReBAC for more dynamic control.
Next Steps
- Explore RBAC implementation in your RobotOps environment using tools like Kubernetes or AWS IAM.
- Conduct a role analysis to align RBAC with your organization’s needs.
- Stay updated on emerging access control models like MCP RBAC for AI-driven robotics.
Resources
- Official Kubernetes RBAC Documentation: kubernetes.io/docs/reference/access-authn-authz/rbac/
- AWS IAM RBAC Guide: aws.amazon.com/iam/
- NIST RBAC Standard: csrc.nist.gov/projects/role-based-access-control
- Open Policy Agent Community: openpolicyagent.org