Introduction & Overview
What is Hardware Root of Trust?
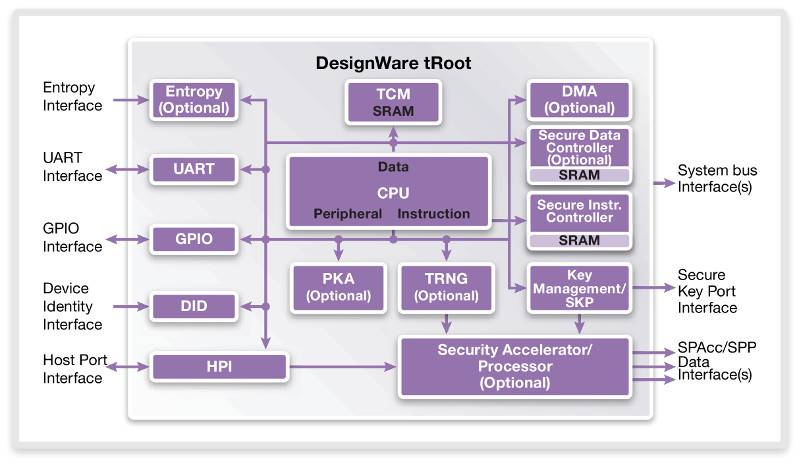
A Hardware Root of Trust (HRoT) is a set of highly reliable hardware, firmware, and software components designed to perform critical security functions, forming a trusted foundation for secure operations in a computing system. It ensures the authenticity, integrity, and confidentiality of devices by providing immutable, tamper-resistant mechanisms for secure boot, key management, and cryptographic operations. In the context of RobotOps (Robotics Operations), HRoT is pivotal for securing robotic systems that operate autonomously or in interconnected environments, such as industrial automation, autonomous vehicles, or collaborative robots (cobots).
History or Background
The concept of HRoT emerged from the need to secure computing systems against evolving cyber threats. Its development can be traced through key milestones:
- Early 2000s: The Trusted Computing Group (TCG) introduced the Trusted Platform Module (TPM), a hardware-based security module that laid the groundwork for HRoT concepts. TPMs provided secure storage for cryptographic keys and supported secure boot processes.
- 2010s: With the rise of IoT and connected devices, the need for robust security in resource-constrained environments led to advancements in HRoT architectures, such as ARM TrustZone and Intel’s Platform Firmware Resilience (PFR).
- 2016–2020: The proliferation of IoT and robotics highlighted vulnerabilities in firmware and software, prompting companies like Rambus and Synopsys to develop programmable HRoT solutions tailored for specific use cases, including IoT and robotics.
- 2020–Present: HRoT has evolved to include quantum-safe cryptography and support for zero-trust architectures, addressing modern threats like side-channel attacks and firmware tampering. The integration of HRoT in RobotOps reflects the growing complexity of robotic systems requiring secure, verifiable operations.
Why is it Relevant in RobotOps?
RobotOps, which combines DevOps principles with robotics, focuses on the development, deployment, and operation of robotic systems. HRoT is critical in RobotOps due to:
- Security in Autonomous Systems: Robots often operate in uncontrolled environments (e.g., warehouses, public spaces), making them vulnerable to physical and cyber attacks.
- Firmware Integrity: Ensures that robotic firmware is authentic and untampered, critical for safe operation.
- Data Protection: Safeguards sensitive data, such as sensor inputs or proprietary algorithms, in interconnected robotic ecosystems.
- Regulatory Compliance: Aligns with standards like ISO 26262 (automotive) or IEC 62443 (industrial automation), ensuring safety and security in regulated industries.
Core Concepts & Terminology
Key Terms and Definitions
| Term | Definition |
|---|---|
| Hardware Root of Trust (HRoT) | A tamper-resistant hardware module that serves as the foundation for secure operations, including key storage, secure boot, and cryptographic functions. |
| Secure Boot | A process that verifies the integrity and authenticity of firmware/software before execution, using digital signatures and HRoT. |
| Trusted Execution Environment (TEE) | A secure area within a processor that isolates sensitive operations, often integrated with HRoT. |
| Key Management | The secure generation, storage, and use of cryptographic keys within the HRoT. |
| Attestation | A mechanism to verify the integrity of software or hardware in real-time, often supported by HRoT. |
| TrustZone | ARM’s hardware-based security technology that provides a TEE, often used as an HRoT component. |
How It Fits into the RobotOps Lifecycle
In RobotOps, HRoT integrates across the development, deployment, and operational phases:
- Development: HRoT ensures that robotic firmware is signed and verified during coding and testing.
- Deployment: Secure boot and attestation validate the integrity of software updates before deployment to robotic systems.
- Operation: HRoT protects runtime operations by securing communication channels and monitoring system integrity.
- Maintenance: Facilitates secure firmware updates and key provisioning to maintain system security over time.
Architecture & How It Works
Components
The HRoT architecture typically includes:
- Secure Processor: A dedicated 32-bit processor (e.g., ARC EM CPU or custom RISC-V) for executing trusted code.
- Cryptographic Cores: Hardware modules for encryption, decryption, and digital signatures (e.g., AES, RSA, ECC).
- Secure Storage: Tamper-resistant memory (e.g., e-fused ROM or SRAM) for storing keys and critical data.
- Secure Instruction Controller: Manages access to encrypted program memory, preventing unauthorized code execution.
- Interfaces: Standard interfaces (e.g., AMBA, AXI) for integration with host processors like ARM, RISC-V, or x86.
- Tamper Detection: Mechanisms to detect physical or side-channel attacks, such as voltage or timing attacks.
Internal Workflow
- Initialization: The HRoT starts with an immutable boot block (IBB) in ROM, which verifies the initial firmware signature.
- Secure Boot: The HRoT validates subsequent software layers (e.g., OS, applications) using digital signatures.
- Key Management: Generates and stores cryptographic keys in secure memory, accessible only to hardware.
- Attestation: Periodically verifies the integrity of running software and reports to a centralized system.
- Cryptographic Operations: Performs encryption, decryption, or signing for secure communication and data protection.
Architecture Diagram Description
The HRoT architecture can be visualized as a layered system:
- Layer 1: Immutable Boot Block (IBB) – Stored in ROM, initiates secure boot.
- Layer 2: Secure Processor – Executes trusted code in a TEE, isolated from the main CPU.
- Layer 3: Cryptographic Cores – Handles AES, RSA, or ECC operations.
- Layer 4: Secure Storage – Stores keys and security metadata.
- Layer 5: Interfaces – Connects to the host processor and system bus.
- External Integration: Links to CI/CD pipelines or cloud platforms for updates and attestation.
[ Developer Repo ] → [ CI/CD Build & Sign ] → [ OTA Update Server ]
↓
Signed Firmware
↓
+-------------------+
| Robot Device |
| |
| [ Boot ROM ] |
| ↓ |
| [ HRoT Module ] |
| (TPM/HSM/TEE) |
| ↓ |
| Verify Bootloader|
| ↓ |
| Verify Kernel |
| ↓ |
| Verify Apps |
+-------------------+
↓
[ Cloud Attestation / RobotOps Dashboard ]
Diagram Note: Imagine a block diagram with the HRoT at the center, connected to the host processor via an AMBA interface. The HRoT contains a secure processor, cryptographic cores, and secure memory, with arrows showing the flow from IBB to secure boot and attestation.
Integration Points with CI/CD or Cloud Tools
- CI/CD Pipelines: HRoT integrates with tools like Jenkins or GitLab CI/CD to sign and verify firmware during build and deployment. For example, a pipeline can use HRoT to sign binaries with a private key before deployment.
- Cloud Tools: HRoT supports cloud-based attestation services (e.g., AWS IoT Device Defender) to verify robotic system integrity remotely.
- RobotOps Platforms: Integrates with platforms like ROS (Robot Operating System) to secure node communication and firmware updates.
Installation & Getting Started
Basic Setup or Prerequisites
- Hardware: A System-on-Chip (SoC) with an HRoT module (e.g., Rambus RT-600, Synopsys tRoot).
- Software: Development tools like ARM Keil, GCC for RISC-V, or vendor-specific SDKs.
- Environment: A secure development environment with access to cryptographic key management tools.
- Network: A secure channel for firmware updates and attestation.
Hands-on: Step-by-Step Beginner-Friendly Setup Guide
- Select an HRoT Module: Choose a compatible HRoT (e.g., Synopsys tRoot for ARM-based robots).
- Set Up Development Environment:
# Install ARM Keil or GCC
sudo apt-get install gcc-arm-none-eabi3. Integrate HRoT into SoC:
- Obtain the HRoT IP core from the vendor.
- Integrate it into the SoC design using tools like Vivado or Quartus.
4. Configure Secure Boot:
// Example: Initialize secure boot with RSA signature
#include <secure_boot.h>
void init_secure_boot() {
if (verify_signature(firmware_image, rsa_public_key) == SUCCESS) {
load_firmware(firmware_image);
} else {
halt_system();
}
}5. Provision Keys:
- Use a Hardware Security Module (HSM) to generate and store keys in the HRoT.
# Example: Generate RSA key pair
openssl genrsa -out private_key.pem 20486. Test Attestation:
- Deploy a test application to verify runtime integrity.
#include <attestation.h>
void attest_system() {
if (check_integrity(software_state) == VALID) {
printf("System integrity verified\n");
} else {
trigger_alert();
}
}7. Integrate with CI/CD:
- Configure a Jenkins pipeline to sign firmware during deployment.
pipeline {
stages {
stage('Sign Firmware') {
steps {
sh 'sign_firmware.sh --input firmware.bin --key private_key.pem'
}
}
}
}Real-World Use Cases
- Industrial Robotics:
- Scenario: A factory uses cobots for assembly. HRoT ensures secure firmware updates to prevent tampering, maintaining compliance with IEC 62443.
- Example: Synopsys tRoot verifies firmware integrity during updates, preventing unauthorized code execution.
- Autonomous Vehicles:
- Scenario: An autonomous delivery robot navigates public spaces. HRoT secures sensor data and communication with cloud servers.
- Example: Rambus RT-600 protects cryptographic keys for V2X (vehicle-to-everything) communication.
- Medical Robotics:
- Scenario: A surgical robot processes patient data. HRoT ensures data confidentiality and integrity.
- Example: ARM TrustZone isolates sensitive operations, preventing data breaches.
- Warehouse Automation:
- Scenario: Robots manage inventory in a smart warehouse. HRoT enables secure boot and attestation for remote monitoring.
- Example: Oracle’s HRoT wipes and reinstalls firmware for each new server instance, reducing PDoS risks.
Benefits & Limitations
Key Advantages
| Benefit | Description |
|---|---|
| Tamper Resistance | HRoT uses hardware-based security to prevent physical and cyber attacks. |
| Secure Boot | Ensures only authenticated firmware runs, reducing malware risks. |
| Key Protection | Stores cryptographic keys in secure memory, inaccessible to software. |
| Scalability | Supports diverse architectures (ARM, RISC-V, x86) for various robotic systems. |
Common Challenges or Limitations
| Limitation | Description |
|---|---|
| Cost | HRoT modules increase silicon area and design costs. |
| Complexity | Integration requires expertise in secure hardware design. |
| Limited Flexibility | Immutable components may restrict updates in some cases. |
| Side-Channel Attacks | Advanced attacks (e.g., timing or power analysis) may still pose risks. |
Best Practices & Recommendations
Security Tips
- Regular Updates: Keep HRoT firmware updated to address new vulnerabilities.
- Key Rotation: Periodically rotate cryptographic keys to mitigate risks.
- Tamper Detection: Enable tamper detection mechanisms to alert on physical attacks.
Performance
- Optimize cryptographic operations to minimize latency in real-time robotic systems.
- Use lightweight algorithms (e.g., ECC) for resource-constrained robots.
Maintenance
- Implement automated attestation checks in CI/CD pipelines.
- Monitor system logs for security events using tools like Splunk or ELK Stack.
Compliance Alignment
- Align with standards like ISO 26262 for automotive or FIPS 140-2 for cryptography.
- Document HRoT processes for audits in regulated industries.
Automation Ideas
- Automate firmware signing in CI/CD pipelines using HSMs.
- Use cloud-based attestation services for real-time integrity checks.
Comparison with Alternatives
| Feature | Hardware Root of Trust | Software Root of Trust | Trusted Platform Module (TPM) |
|---|---|---|---|
| Security Level | High (hardware-based) | Medium (software-based) | High (dedicated chip) |
| Integration | SoC-integrated | OS-level | External chip |
| Cost | High | Low | Moderate |
| Flexibility | Limited (immutable) | High | Moderate |
| Use Case | Robotics, IoT | General-purpose computing | PCs, servers |
When to Choose HRoT
- Choose HRoT: For robotics requiring high security, tamper resistance, and compliance (e.g., autonomous vehicles, medical robots).
- Choose Alternatives: Use software RoT for less critical applications or TPM for legacy systems with external security modules.
Conclusion
Final Thoughts
Hardware Root of Trust is a cornerstone of secure RobotOps, providing a trusted foundation for robotic systems in diverse applications. By ensuring firmware integrity, protecting keys, and enabling secure communication, HRoT addresses the unique security challenges of robotics in interconnected environments.
Future Trends
- Quantum-Safe Cryptography: HRoT modules are adopting quantum-resistant algorithms to counter future threats.
- Zero-Trust Integration: HRoT will play a key role in zero-trust architectures for RobotOps.
- AI-Driven Security: Integration with AI for real-time threat detection and response.
Next Steps
- Explore vendor documentation (e.g., Rambus, Synopsys) for specific HRoT implementations.
- Join communities like the Trusted Computing Group (TCG) for updates on HRoT standards.
- Experiment with HRoT in a test environment using open-source tools like OpenTitan.