Introduction & Overview
Secure Boot is a critical security mechanism designed to ensure that a device boots only with trusted software by verifying the integrity and authenticity of the firmware and operating system during the startup process. In the context of RobotOps, which refers to the operational and development practices for robotics systems (primarily using the Robot Operating System, ROS), Secure Boot plays a pivotal role in safeguarding robotic systems from unauthorized code execution, especially in networked and autonomous environments. This tutorial provides a detailed exploration of Secure Boot in RobotOps, covering its concepts, implementation, use cases, benefits, limitations, and best practices.
What is Secure Boot?
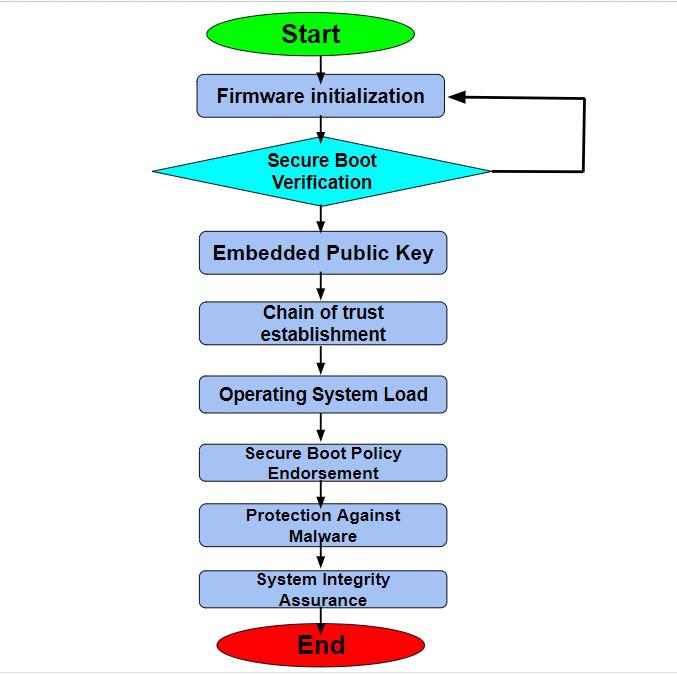
Secure Boot is a security standard that ensures a device only boots using software that is trusted by the Original Equipment Manufacturer (OEM). It leverages cryptographic signatures to verify each component in the boot process, preventing malicious or unverified code from executing.
- Core Functionality: Verifies digital signatures of boot components (e.g., bootloader, kernel, firmware) against trusted public keys embedded in the hardware.
- Purpose: Protects against rootkits, bootkits, and unauthorized firmware modifications that could compromise system integrity.
- Mechanism: Uses a chain of trust, where each boot stage verifies the next before execution, starting from a hardware-based root of trust.
History or Background
Secure Boot was introduced as part of the Unified Extensible Firmware Interface (UEFI) specification by the UEFI Forum in 2011 to address growing security concerns in traditional BIOS-based systems. Its development was driven by the rise of sophisticated malware targeting the boot process, such as rootkits.
- Early Development: Microsoft championed Secure Boot for Windows 8 in 2012, integrating it into UEFI to secure PCs against boot-time attacks.
- Adoption in Embedded Systems: Secure Boot gained traction in embedded systems, including IoT devices and robotics, due to the need for secure firmware updates in networked environments.
- ROS Context: With the rise of ROS (introduced in 2007 by Willow Garage) and ROS 2 (introduced in 2017), Secure Boot became relevant for robotics to ensure trusted software execution in autonomous vehicles, industrial robots, and drones. The increasing reliance on ROS in networked environments necessitated robust boot security to prevent tampering.
Why is it Relevant in RobotOps?
RobotOps involves managing the lifecycle of robotic systems, including development, deployment, monitoring, and maintenance, often using ROS or ROS 2. Secure Boot is critical in RobotOps for the following reasons:
- Protection Against Threats: Robots, especially in industrial, medical, or autonomous vehicle applications, are high-value targets for cyberattacks that could manipulate firmware or ROS nodes.
- Ensuring System Integrity: Secure Boot ensures that only verified ROS-based software runs, critical for safety-critical applications like autonomous navigation.
- Regulatory Compliance: Industries like automotive (e.g., ISO 26262) and medical robotics require secure boot processes to meet safety and security standards.
- Remote Firmware Updates: RobotOps often involves over-the-air (OTA) updates, where Secure Boot ensures that only authentic updates are applied, preventing malicious code injection.
Core Concepts & Terminology
Key Terms and Definitions
- Root of Trust: A hardware-based security anchor (e.g., Trusted Platform Module, TPM) that stores cryptographic keys for Secure Boot.
- Chain of Trust: A sequence where each boot component verifies the next, ensuring no untrusted code executes.
- Public Key Infrastructure (PKI): A system for managing digital certificates and keys used to sign and verify boot components.
- UEFI: Unified Extensible Firmware Interface, the modern replacement for BIOS, which includes Secure Boot capabilities.
- Bootloader: Software that loads the operating system; in Secure Boot, it verifies the kernel’s signature.
- ROS Node: A modular process in ROS that performs specific tasks, such as sensor data processing or motor control.
| Term | Definition |
|---|---|
| UEFI | Modern firmware replacing BIOS, enabling Secure Boot. |
| Bootloader | First piece of software loaded after firmware; validates OS kernel. |
| PK (Platform Key) | Root key used by the OEM to sign/validate firmware. |
| KEK (Key Exchange Key) | Key set used to manage updates to Secure Boot keys. |
| db (Allow List) | Database of allowed (trusted) OS loaders and drivers. |
| dbx (Deny List) | Database of revoked signatures (malware, compromised certs). |
| Measured Boot | A related concept where each boot stage is measured (hashed) for attestation. |
| Chain of Trust | Security model where each stage verifies the next (firmware → bootloader → OS kernel → drivers). |
How It Fits into the RobotOps Lifecycle
Secure Boot integrates into the RobotOps lifecycle across several stages:
- Development: Developers sign ROS-based firmware and software with private keys to ensure authenticity.
- Deployment: Secure Boot verifies the integrity of deployed ROS images on robotic hardware (e.g., Raspberry Pi, NVIDIA Jetson).
- Maintenance: OTA updates in RobotOps require Secure Boot to validate new firmware versions.
- Monitoring: Secure Boot logs can be integrated with RobotOps monitoring tools to detect boot-time anomalies.
Architecture & How It Works
Components and Internal Workflow
Secure Boot in RobotOps involves the following components:
- Hardware Root of Trust: A secure hardware module (e.g., TPM or secure enclave) storing public keys or certificates.
- Bootloader: A UEFI-compliant bootloader (e.g., U-Boot, GRUB) that verifies the OS kernel’s signature.
- Operating System Kernel: Typically a Linux-based OS (e.g., Ubuntu, used with ROS) with a signed kernel image.
- Cryptographic Keys: Public/private key pairs for signing and verifying boot components.
- ROS/ROS 2 Middleware: The ROS framework running on the verified OS, managing robotic operations.
Workflow:
- Power-On: The hardware root of trust initializes and loads the UEFI firmware.
- Firmware Verification: The UEFI firmware verifies the bootloader’s digital signature using embedded public keys.
- Bootloader Execution: The verified bootloader checks the OS kernel’s signature.
- Kernel Loading: If valid, the kernel loads, initializing the ROS environment.
- Failure Handling: If any signature verification fails, the system halts or boots into a recovery mode.
Architecture Diagram
Below is a textual description of the Secure Boot architecture in RobotOps (as image generation is not possible):
+---------------------+
| Hardware Layer |
+---------------------+
↓
+---------------------+
| UEFI Firmware |
| - Secure Boot Keys |
+---------------------+
↓
+---------------------+
| Bootloader |
| (Verified) |
+---------------------+
↓
+---------------------+
| OS Kernel |
| (Verified) |
+---------------------+
↓
+---------------------+
| Robot Drivers & Libs|
| (Trusted Only) |
+---------------------+
↓
+---------------------+
| RobotOps Runtime |
+---------------------+
Explanation:
- The Hardware Root of Trust anchors the chain of trust, storing public keys.
- UEFI Firmware verifies the bootloader.
- The Bootloader validates the kernel, which hosts the ROS environment.
- ROS/ROS 2 Nodes operate within the secure environment.
- The CI/CD Pipeline integrates with Secure Boot for signed OTA updates.
Integration Points with CI/CD or Cloud Tools
- CI/CD Integration: Tools like Jenkins or GitLab CI/CD can automate signing of ROS images using private keys stored in secure vaults (e.g., AWS KMS, HashiCorp Vault).
- Cloud Tools: AWS IoT Greengrass or Azure IoT Edge can integrate with Secure Boot for OTA updates, ensuring only signed firmware is deployed.
- Monitoring: ROS nodes can publish boot logs to cloud platforms (e.g., AWS CloudWatch) for anomaly detection.
Installation & Getting Started
Basic Setup or Prerequisites
- Hardware: A device with UEFI support and a TPM (e.g., Raspberry Pi 4, NVIDIA Jetson Nano).
- Operating System: Ubuntu 20.04 or later (ROS 2 recommended).
- Tools:
efibootmgrfor UEFI configuration.sbsignfor signing boot components.- OpenSSL for key generation.
- ROS/ROS 2: Installed and configured (e.g., ROS 2 Humble).
- Network: Secure network for OTA updates.
Hands-On: Step-by-Step Beginner-Friendly Setup Guide
Below is a step-by-step guide to set up Secure Boot on a Raspberry Pi 4 running Ubuntu with ROS 2:
- Generate Cryptographic Keys:
openssl genrsa -out private_key.pem 2048
openssl rsa -in private_key.pem -pubout -out public_key.pem2. Configure UEFI on Raspberry Pi:
- Enable UEFI firmware on the Raspberry Pi by updating the bootloader to a UEFI-compatible version (e.g., EDK2).
- Copy
public_key.pemto the TPM or secure storage.
3. Sign the Bootloader and Kernel:
sbsign --key private_key.pem --cert public_key.pem --output vmlinuz-signed /boot/vmlinuz
sbsign --key private_key.pem --cert public_key.pem --output grub-signed /boot/grub/grub.efi4. Configure UEFI Boot Entries:
efibootmgr -c -d /dev/sdX -p 1 -L "Secure ROS Boot" -l "\EFI\ubuntu\grub-signed.efi"5. Install ROS 2:
sudo apt update
sudo apt install ros-humble-desktop6. Test Secure Boot:
- Reboot the device.
- Verify that the system boots only with signed components. If an unsigned kernel is used, the boot should fail.
7. Integrate with RobotOps Pipeline:
- Use a CI/CD tool to automate signing and deployment of ROS images.
# Example Jenkins pipeline step
stage('Sign ROS Image') {
sh 'sbsign --key private_key.pem --cert public_key.pem --output ros_image_signed /path/to/ros_image'
}Real-World Use Cases
- Autonomous Vehicles:
- Scenario: A self-driving car uses ROS 2 for sensor fusion and navigation. Secure Boot ensures that only verified firmware runs, preventing malicious code from altering path planning.
- Industry: Automotive (e.g., DARPA Urban Challenge).
- Implementation: The vehicle’s ECU uses a TPM to verify the ROS 2 kernel, ensuring safe operation.
- Industrial Robotics:
- Medical Robotics:
- Scenario: A surgical robot uses ROS 2 for precision control. Secure Boot ensures that only trusted software runs, critical for patient safety.
- Industry: Healthcare.
- Implementation: The robot’s firmware is signed and verified using a hardware root of trust.
- Drones:
- Scenario: A drone running ROS 2 for aerial mapping uses Secure Boot to protect against firmware tampering during OTA updates.
- Industry: Aerospace.
- Implementation: The drone’s flight controller verifies the ROS 2 image before takeoff.
Benefits & Limitations
Key Advantages
- Enhanced Security: Prevents unauthorized code execution, critical for safety-critical robotic systems.
- Trust Assurance: Ensures that only OEM-verified software runs, reducing the risk of supply chain attacks.
- Compliance: Aligns with standards like ISO 26262 and IEC 62443 for automotive and industrial applications.
- OTA Update Safety: Validates firmware updates, ensuring reliability in RobotOps pipelines.
Common Challenges or Limitations
- Complexity: Setting up Secure Boot requires expertise in UEFI, PKI, and ROS integration.
- Performance Overhead: Signature verification adds boot-time latency, which may impact real-time systems.
- Key Management: Secure storage and management of private keys are critical but challenging.
- Compatibility: Not all robotic hardware supports UEFI or TPM, limiting adoption in legacy systems.
| Aspect | Benefit | Limitation |
|---|---|---|
| Security | Prevents unauthorized code execution | Requires complex key management |
| Performance | Ensures trusted boot process | Adds boot-time latency |
| Compatibility | Supports modern robotic platforms | Limited support for legacy hardware |
| Maintenance | Enables secure OTA updates | Requires expertise for setup and updates |
Best Practices & Recommendations
- Security Tips:
- Use a dedicated TPM or secure enclave for key storage.
- Regularly rotate cryptographic keys and audit signatures.
- Implement secure key provisioning in the RobotOps pipeline.
- Performance:
- Optimize bootloader for minimal verification latency.
- Use lightweight cryptographic algorithms (e.g., SHA-256) suitable for embedded systems.
- Maintenance:
- Automate signing and verification in CI/CD pipelines using tools like Jenkins or GitLab.
- Monitor boot logs for anomalies using ROS diagnostic nodes.
- Compliance Alignment:
- Align with ISO 26262 for automotive or IEC 62443 for industrial robotics.
- Document Secure Boot processes for audits.
- Automation Ideas:
- Integrate Secure Boot with ROS 2’s DDS security for end-to-end protection.
- Use cloud-based key management services (e.g., AWS KMS) for OTA updates.
Comparison with Alternatives
| Feature | Secure Boot | Trusted Execution Environment (TEE) | Software-Based Verification |
|---|---|---|---|
| Security Level | High (hardware-based) | High (isolated execution) | Medium (software-based) |
| Hardware Dependency | Requires TPM/UEFI | Requires TEE (e.g., ARM TrustZone) | None |
| Performance Overhead | Moderate (boot-time verification) | Low (runtime isolation) | Low (minimal overhead) |
| ROS Integration | Verifies OS and ROS image | Protects ROS node execution | Limited to application layer |
| Use Case | Boot-time security | Runtime security | Basic integrity checks |
When to Choose Secure Boot
- Choose Secure Boot: For robotics systems requiring boot-time integrity, especially in safety-critical applications (e.g., autonomous vehicles, medical robots).
- Choose Alternatives: Use TEE for runtime security or software-based verification for non-critical, legacy systems without UEFI support.
Conclusion
Secure Boot is a cornerstone of RobotOps security, ensuring that ROS-based robotic systems boot with trusted software, protecting against tampering and ensuring compliance. Its integration into the RobotOps lifecycle enhances reliability and safety, particularly for autonomous and industrial applications. Future trends include tighter integration with ROS 2’s DDS security and advancements in lightweight cryptographic algorithms for embedded systems.
Next Steps:
- Explore ROS 2 security features for complementary protection.
- Experiment with Secure Boot on a Raspberry Pi or NVIDIA Jetson.
- Join the ROS community for updates and best practices.
Resources: